Mercredi 21 mars 2018
Chrome Extension Protects Against JavaScript-Based CPU Side-Channel Attacks
A team of academics has created a Chrome extension that can block side-channel attacks that use JavaScript code to leak data from a computer's RAM or CPU.
The extension's name is Chrome Zero and is currently only available on GitHub, and not through the official Chrome Web Store.
Researchers created the extension to rewrite and protect JavaScript functions, properties, and objects that are often used by malicious JavaScript code aimed at leaking CPU or memory data.
Extension blocks 11 JavaScript-based side-channel attacks
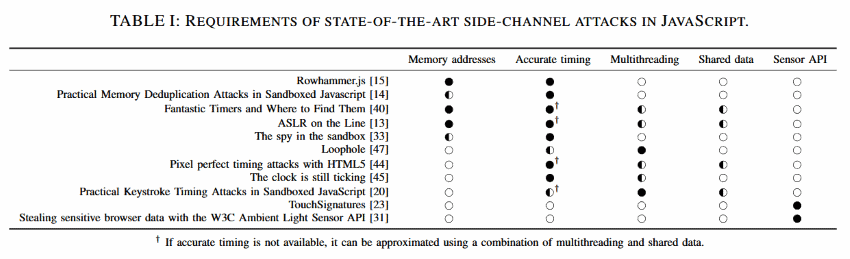
Experts say that currently there are eleven state-of-the-art side-channel attacks that can be performed via JavaScript code running in a browser.
Each attack needs access to various local details, for which it uses JavaScript code to leak, recover, and gather the needed information before mounting the actual side-channel attack.
After looking at each of the eleven attacks, researchers say they've identified five main categories of data/features that JavaScript side-channel attacks attempt to exploit: JS-recoverable memory addresses, accurate timing (time difference) information, the browser's multithreading (web workers) support, data shared among JS code threads, and data from device sensors.
 The Chrome Zero extension works by intercepting the JavaScript code the Chrome browser is supposed to execute and rewriting certain JavaScript functions, properties, and objects in a wrapper that neutralizes its negative effects, which a side-channel attack would try to leverage.
Chrome Zero has a minimum performance impact
Experts said that despite the extension's intrusive behavior, tests showed a minimum performance impact of only 1.54% on resource usage, and an indiscernible page loading latency ranging from 0.01064s and 0.08908s —depending on the number of protection policies active at runtime.
Furthermore, as a side-effect of the extension's "protective measures," the research team says Chrome Zero would have been able to block 50% of the Chrome zero-days detected in the real world since the release of Chrome 49.
The extension may be very well able to thwart even future and unknown Chrome zero-days as well, mainly because of its habit of rewriting dangerous functions to safer versions.
How to install Chrome Zero
Since the extension is not yet on the Chrome Web Store, users can install it by (1) downloading the extension's source code from GitHub, (2) going to Chrome's extensions management page (chrome://extensions), (3) enabling "Developer Mode," (4) clicking "Load Unpacked," and (5) selecting the folder "/chromezero" from inside the extension's source code.
The Chrome Zero extension works by intercepting the JavaScript code the Chrome browser is supposed to execute and rewriting certain JavaScript functions, properties, and objects in a wrapper that neutralizes its negative effects, which a side-channel attack would try to leverage.
Chrome Zero has a minimum performance impact
Experts said that despite the extension's intrusive behavior, tests showed a minimum performance impact of only 1.54% on resource usage, and an indiscernible page loading latency ranging from 0.01064s and 0.08908s —depending on the number of protection policies active at runtime.
Furthermore, as a side-effect of the extension's "protective measures," the research team says Chrome Zero would have been able to block 50% of the Chrome zero-days detected in the real world since the release of Chrome 49.
The extension may be very well able to thwart even future and unknown Chrome zero-days as well, mainly because of its habit of rewriting dangerous functions to safer versions.
How to install Chrome Zero
Since the extension is not yet on the Chrome Web Store, users can install it by (1) downloading the extension's source code from GitHub, (2) going to Chrome's extensions management page (chrome://extensions), (3) enabling "Developer Mode," (4) clicking "Load Unpacked," and (5) selecting the folder "/chromezero" from inside the extension's source code.
 Once the extension has been loaded and enabled, users can select their desired protection level.
Chrome Zero protection settings
The academics who created Chrome Zero are also the ones behind the JavaScript-version of the Rowhammer attack and have also contributed to the discovery of the Meltdown and Spectre vulnerabilities.
More details on their most recent research are available in a paper entitled "JavaScript Zero: Real JavaScript and Zero Side-Channel Attacks," presented at the end of February at the NDSS Symposium in San Diego, California. The paper is available online here and here, and a video of the NDSS presentation is also embedded below.
Source : https://www.bleepingcomputer.com/news/security/chrome-extension-protects-against-javascript-based-cpu-side-channel-attacks/
Once the extension has been loaded and enabled, users can select their desired protection level.
Chrome Zero protection settings
The academics who created Chrome Zero are also the ones behind the JavaScript-version of the Rowhammer attack and have also contributed to the discovery of the Meltdown and Spectre vulnerabilities.
More details on their most recent research are available in a paper entitled "JavaScript Zero: Real JavaScript and Zero Side-Channel Attacks," presented at the end of February at the NDSS Symposium in San Diego, California. The paper is available online here and here, and a video of the NDSS presentation is also embedded below.
Source : https://www.bleepingcomputer.com/news/security/chrome-extension-protects-against-javascript-based-cpu-side-channel-attacks/
 The Chrome Zero extension works by intercepting the JavaScript code the Chrome browser is supposed to execute and rewriting certain JavaScript functions, properties, and objects in a wrapper that neutralizes its negative effects, which a side-channel attack would try to leverage.
Chrome Zero has a minimum performance impact
Experts said that despite the extension's intrusive behavior, tests showed a minimum performance impact of only 1.54% on resource usage, and an indiscernible page loading latency ranging from 0.01064s and 0.08908s —depending on the number of protection policies active at runtime.
Furthermore, as a side-effect of the extension's "protective measures," the research team says Chrome Zero would have been able to block 50% of the Chrome zero-days detected in the real world since the release of Chrome 49.
The extension may be very well able to thwart even future and unknown Chrome zero-days as well, mainly because of its habit of rewriting dangerous functions to safer versions.
How to install Chrome Zero
Since the extension is not yet on the Chrome Web Store, users can install it by (1) downloading the extension's source code from GitHub, (2) going to Chrome's extensions management page (chrome://extensions), (3) enabling "Developer Mode," (4) clicking "Load Unpacked," and (5) selecting the folder "/chromezero" from inside the extension's source code.
The Chrome Zero extension works by intercepting the JavaScript code the Chrome browser is supposed to execute and rewriting certain JavaScript functions, properties, and objects in a wrapper that neutralizes its negative effects, which a side-channel attack would try to leverage.
Chrome Zero has a minimum performance impact
Experts said that despite the extension's intrusive behavior, tests showed a minimum performance impact of only 1.54% on resource usage, and an indiscernible page loading latency ranging from 0.01064s and 0.08908s —depending on the number of protection policies active at runtime.
Furthermore, as a side-effect of the extension's "protective measures," the research team says Chrome Zero would have been able to block 50% of the Chrome zero-days detected in the real world since the release of Chrome 49.
The extension may be very well able to thwart even future and unknown Chrome zero-days as well, mainly because of its habit of rewriting dangerous functions to safer versions.
How to install Chrome Zero
Since the extension is not yet on the Chrome Web Store, users can install it by (1) downloading the extension's source code from GitHub, (2) going to Chrome's extensions management page (chrome://extensions), (3) enabling "Developer Mode," (4) clicking "Load Unpacked," and (5) selecting the folder "/chromezero" from inside the extension's source code.
 Once the extension has been loaded and enabled, users can select their desired protection level.
Chrome Zero protection settings
The academics who created Chrome Zero are also the ones behind the JavaScript-version of the Rowhammer attack and have also contributed to the discovery of the Meltdown and Spectre vulnerabilities.
More details on their most recent research are available in a paper entitled "JavaScript Zero: Real JavaScript and Zero Side-Channel Attacks," presented at the end of February at the NDSS Symposium in San Diego, California. The paper is available online here and here, and a video of the NDSS presentation is also embedded below.
Source : https://www.bleepingcomputer.com/news/security/chrome-extension-protects-against-javascript-based-cpu-side-channel-attacks/
Once the extension has been loaded and enabled, users can select their desired protection level.
Chrome Zero protection settings
The academics who created Chrome Zero are also the ones behind the JavaScript-version of the Rowhammer attack and have also contributed to the discovery of the Meltdown and Spectre vulnerabilities.
More details on their most recent research are available in a paper entitled "JavaScript Zero: Real JavaScript and Zero Side-Channel Attacks," presented at the end of February at the NDSS Symposium in San Diego, California. The paper is available online here and here, and a video of the NDSS presentation is also embedded below.
Source : https://www.bleepingcomputer.com/news/security/chrome-extension-protects-against-javascript-based-cpu-side-channel-attacks/


